A) {"key": "value"}
B) ["key", "value"]
C) {"key", "value"}
D) ("key": "value")
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
When deploying syslog, which severity level logs informational messages?
A) 0
B) 2
C) 4
D) 6
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
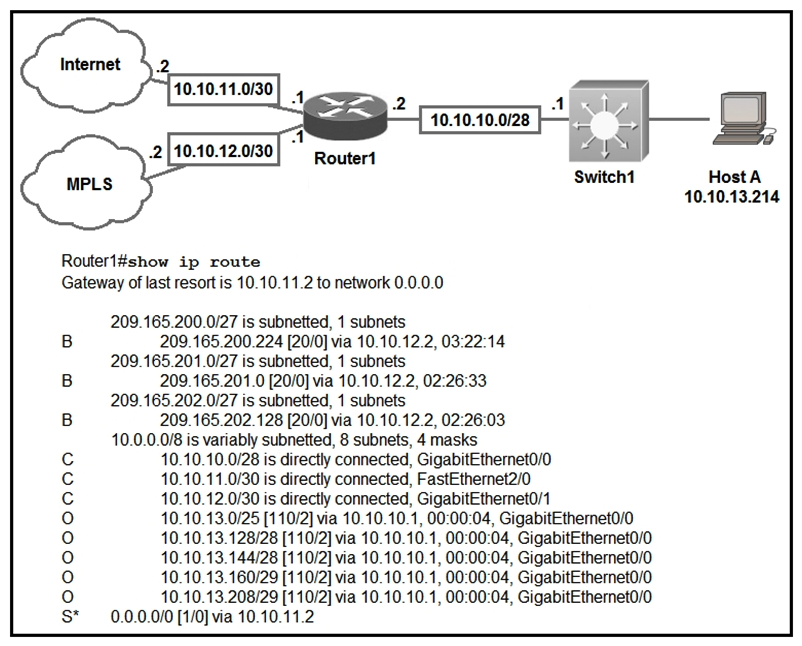 Refer to the exhibit. Which prefix does Router1 use for traffic to Host A?
Refer to the exhibit. Which prefix does Router1 use for traffic to Host A?
A) 10.10.10.0/28
B) 10.10.13.0/25
C) 10.10.13.144/28
D) 10.10.13.208/29
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the function of a server?
A) It transmits packets between hosts in the same broadcast domain.
B) It provides shared applications to end users.
C) It routes traffic between Layer 3 devices.
D) It Creates security zones between trusted and untrusted networks.
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which three describe the reasons large OSPF networks use a hierarchical design? (Choose three.)
A) to speed up convergence
B) to reduce routing overhead
C) to lower costs by replacing routers with distribution layer switches
D) to decrease latency by increasing bandwidth
E) to confine network instability to single areas of the network
F) to reduce the complexity of router configuration
H) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which security program element involves installing badge readers on data-center doors to allow workers to enter and exit based on their job roles?
A) physical access control
B) biometrics
C) role-based access control
D) multifactor authentication
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two roles of the Dynamic Host Configuration Protocol (DHCP) ? (Choose two.)
A) The DHCP server assigns IP addresses without requiring the client to renew them.
B) The DHCP server leases client IP addresses dynamically.
C) The DHCP client can request up to four DNS server addresses.
D) The DHCP server offers the ability to exclude specific IP addresses from a pool of IP addresses.
E) The DHCP client maintains a pool of IP addresses it can assign.
G) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What are two differences between optical-fiber cabling and copper cabling? (Choose two.)
A) A BNC connector is used for fiber connections
B) The glass core component is encased in a cladding
C) The data can pass through the cladding
D) Light is transmitted through the core of the fiber
E) Fiber connects to physical interfaces using RJ-45 connections
G) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which protocol is used in Software Defined Access (SDA) to provide a tunnel between two edge nodes in different fabrics?
A) Generic Router Encapsulation (GRE)
B) Virtual Local Area Network (VLAN)
C) Virtual Extensible LAN (VXLAN)
D) Point-to-Point Protocol (PPP)
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which option about JSON is true
A) uses predefined tags or angle brackets () to delimit markup text
B) used to describe structured data that includes arrays
C) used for storing information
D) similar to HTML, it is more verbose than XML
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two actions are performed by the Weighted Random Early Detection mechanism? (Choose two.)
A) It supports protocol discovery.
B) It guarantees the delivery of high-priority packets.
C) It can identify different flows with a high level of granularity.
D) It can mitigate congestion by preventing the queue from filling up.
E) It drops lower-priority packets before it drops higher-priority packets.
G) B) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which NAT term is defined as a group of addresses available for NAT use?
A) NAT pool
B) dynamic NAT
C) static NAT
D) one-way NAT
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
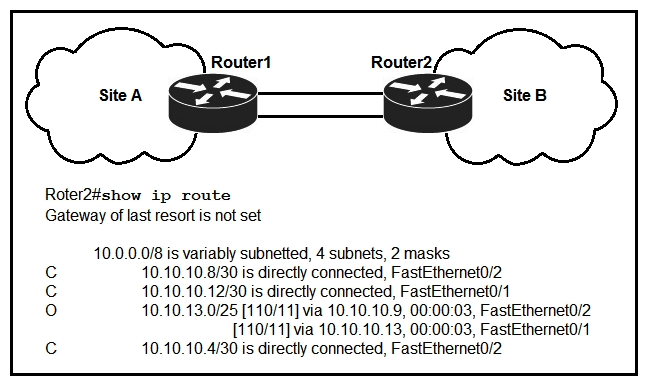 Refer to the exhibit. If OSPF is running on this network, how does Router2 handle traffic from Site B to 10.10.13.128/25 at Site A?
Refer to the exhibit. If OSPF is running on this network, how does Router2 handle traffic from Site B to 10.10.13.128/25 at Site A?
A) It sends packets out of interface Fa0/1 only.
B) It sends packets out of interface Fa0/2 only.
C) It load-balances traffic out of Fa0/1 and Fa0/2.
D) It cannot send packets to 10.10.13.128/25.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
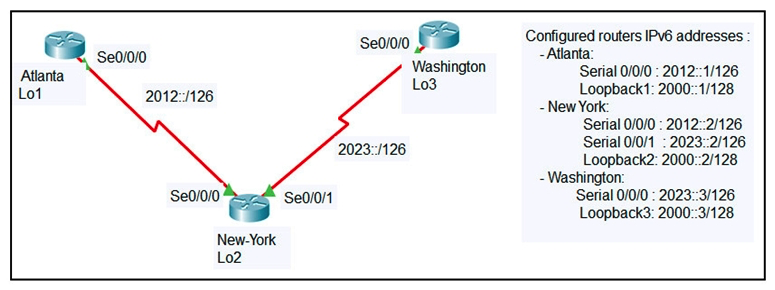 Refer to the exhibit. An engineer configured the New York router with static routes that point to the Atlanta and Washington sites. Which command must be configured on the Atlanta and Washington routers so that both sites are able to reach the loopback2 interface on the New York router?
Refer to the exhibit. An engineer configured the New York router with static routes that point to the Atlanta and Washington sites. Which command must be configured on the Atlanta and Washington routers so that both sites are able to reach the loopback2 interface on the New York router?
A) ipv6 route::/0 Serial 0/0/0
B) ipv6 route::/0 Serial 0/0/1
C) ipv6 route:0/0 Serial 0/0/0
D) ip route 0.0.0.0 0.0.0.0 Serial 0/0/0
E) ipv6 route::/0 2000::2
G) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network administrator enters the following command on a router: logging trap 3. What are three message types that will be sent to the Syslog server? (Choose three.)
A) informational
B) emergency
C) warning
D) critical
E) debug
F) error
H) D) and F)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which plane is centralized by an SDN controller?
A) management-plane
B) data-plane
C) services-plane
D) control-plane
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have implemented a dynamic blacklist, using security intelligence to block illicit network activity. However, the blacklist contains several approved connections that users must access for business purposes. Which action can you take to retain the blacklist while allowing users to access the approved sites?
A) Create a whitelist and manually add the approved addresses
B) Edit the dynamic blacklist to remove the approved addresses
C) Disable the dynamic blacklist and deny the specific address on a whitelist while permitting the others
D) Disable the dynamic blacklist and create a static blacklist in its place
F) A) and B)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. Router R1 is running three different routing protocols. Which route characteristic is used by the router to forward the packet that it receives for destination IP 172.16.32.1? 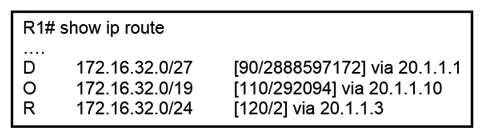
A) longest prefix
B) administrative distance
C) cost
D) metric
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which design element is a best practice when deploying an 802.11b wireless infrastructure?
A) allocating nonoverlapping channels to access points that are in close physical proximity to one another
B) disabling TCP so that access points can negotiate signal levels with their attached wireless devices
C) configuring access points to provide clients with a maximum of 5 Mbps
D) setting the maximum data rate to 54 Mbps on the Cisco Wireless LAN Controller
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the primary effect of the spanning-tree portfast command?
A) It immediately enables the port in the listening state.
B) It immediately puts the port into the forwarding state when the switch is reloaded.
C) It enables BPDU messages.
D) It minimizes spanning-tree convergence time.
F) All of the above
Correct Answer

verified
Correct Answer
verified
Showing 261 - 280 of 411
Related Exams