A) facilitates communication between the controller and the applications
B) reports device errors to a controller
C) generates statistics for network hardware and traffic
D) communicates between the controller and the physical network hardware
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two pieces of information can you determine from the output of the show ntp status command? (Choose two.)
A) whether the NTP peer is statically configured
B) the IP address of the peer to which the clock is synchronized
C) the configured NTP servers
D) whether the clock is synchronized
E) the NTP version number of the peer
G) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which command can you enter to determine the addresses that have been assigned on a DHCP Server?
A) Show ip DHCP database.
B) Show ip DHCP pool.
C) Show ip DHCP binding.
D) Show ip DHCP server statistic.
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. Which two statements are true about the loopback address that is configured on RouterB? (Choose two.) 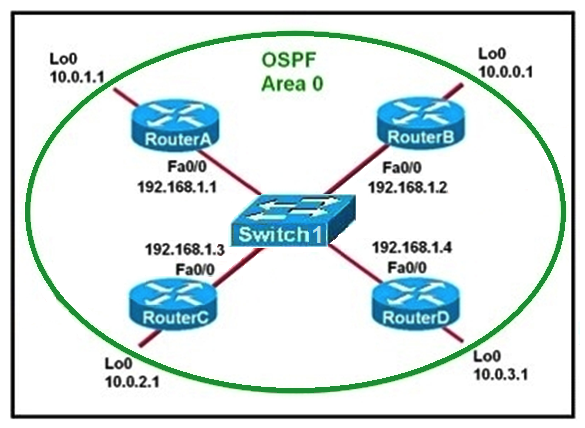
A) It ensures that data will be forwarded by RouterB.
B) It provides stability for the OSPF process on RouterB.
C) It specifies that the router ID for RouterB should be 10.0.0.1.
D) It decreases the metric for routes that are advertised from RouterB.
E) It indicates that RouterB should be elected the DR for the LAN.
G) A) and E)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How will Link Aggregation be implemented on a Cisco Wireless LAN Controller?
A) The EtherChannel must be configured in "mode active".
B) When enabled, the WLC bandwidth drops to 500 Mbps.
C) To pass client traffic, two or more ports must be configured.
D) One functional physical port is needed to pass client traffic.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
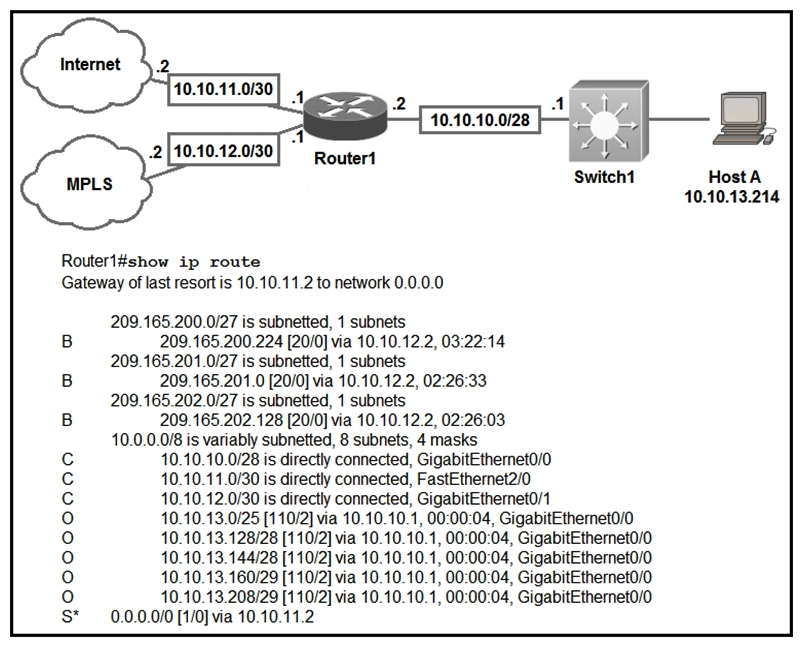 Refer to the exhibit. Which prefix does Router1 use to Host A?
Refer to the exhibit. Which prefix does Router1 use to Host A?
A) 10.10.10.0/28
B) 10.10.13.0/25
C) 10.10.13.144/28
D) 10.10.13.208/29
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which two QoS tools provide congestion management? (Choose two.)
A) CBWFQ
B) FRTS
C) CAR
D) PBR
E) PQ
G) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
You have two paths for the 10.10.10.0 network - one that has a feasible distance of 3072 and the other of 6144. What do you need to do to load balance your EIGRP routes?
A) Change the maximum paths to 2
B) Change the configuration so they both have the same feasible distance
C) Change the variance for the path that has a feasible distance of 3072 to 2
D) Change the IP addresses so both paths have the same source IP address
F) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
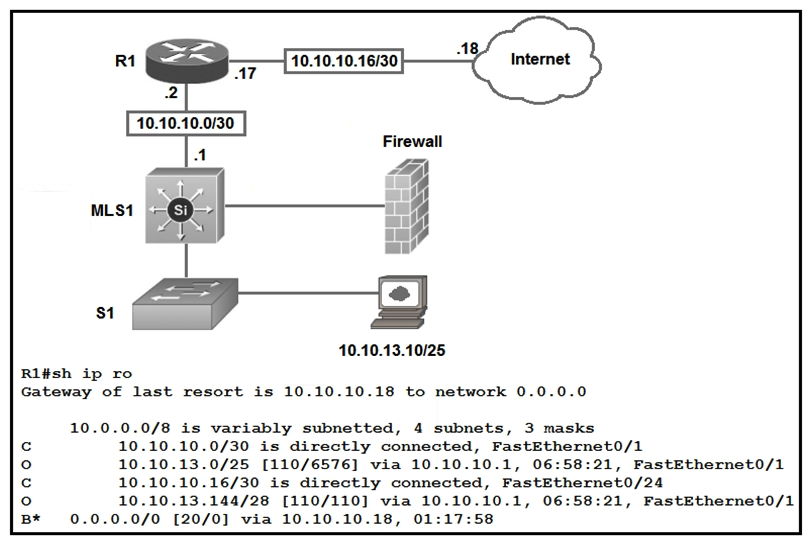 Refer to the exhibit. Which type of route does R1 use to reach host 10.10.13.10/32?
Refer to the exhibit. Which type of route does R1 use to reach host 10.10.13.10/32?
A) default route
B) network route
C) host route
D) floating static route
F) A) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. An administrator is tasked with configuring a voice VLAN. What is the expected outcome when a Cisco phone is connected to the GigabitEthernet 3/1/4 port on a switch? 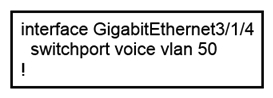
A) The phone and a workstation that is connected to the phone do not have VLAN connectivity.
B) The phone sends and receives data in VLAN 50, but a workstation connected to the phone sends and receives data in VLAN 1.
C) The phone sends and receives data in VLAN 50, but a workstation connected to the phone has no VLAN connected.
D) The phone and a workstation that is connected to the phone send and receive data in VLAN 50.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
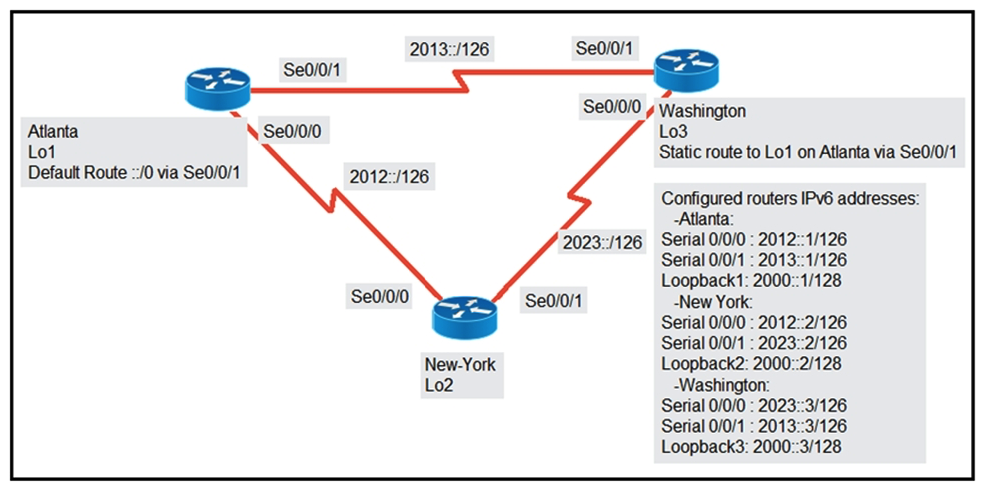 Refer to the exhibit. An engineer is configuring the New York router to reach the Lo1 interface of the Atlanta router using interface Se0/0/0 as the primary path. Which two commands must be configured on the New York router so that it reaches the Lo1 interface of the Atlanta router via Washington when the link between New York and Atlanta goes down? (Choose two.)
Refer to the exhibit. An engineer is configuring the New York router to reach the Lo1 interface of the Atlanta router using interface Se0/0/0 as the primary path. Which two commands must be configured on the New York router so that it reaches the Lo1 interface of the Atlanta router via Washington when the link between New York and Atlanta goes down? (Choose two.)
A) Ipv6 route 2000::1/128 2012::1
B) Ipv6 route 2000::1/128 2012::1 5
C) Ipv6 route 2000::1/128 2012::2
D) Ipv6 route 2000::1/128 2023::2 5
E) Ipv6 route 2000::1/128 2023::3 5
G) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
How do TCP and UDP differ in the way that they establish a connection between two endpoints?
A) TCP uses the three-way handshake, and UDP does not guarantee message delivery.
B) TCP uses synchronization packets, and UDP uses acknowledgment packets.
C) UDP provides reliable message transfer, and TCP is a connectionless protocol.
D) UDP uses SYN, SYN ACK, and FIN bits in the frame header while TCP uses SYN, SYN ACK, and ACK bits.
F) None of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What role does a hypervisor provide for each virtual machine in server virtualization?
A) infrastructure-as-a-service
B) Software-as-a-service
C) control and distribution of physical resources
D) services as a hardware controller
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
What is the purpose of traffic shaping?
A) to be a marking mechanism that identifies different flows
B) to provide fair queuing for buffered flows
C) to mitigate delays over slow links
D) to limit the bandwidth that a flow can use
F) C) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A port security violation has occurred on a switch port due to the maximum MAC address count being exceeded. Which command must be configured to increment the security-violation count and forward an SNMP trap?
A) switchport port-security violation access
B) switchport port-security violation protect
C) switchport port-security violation restrict
D) switchport port-security violation shutdown
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
A) enable dynamic MAC address learning
B) implement static MAC addressing
C) enable sticky MAC addressing
D) implement auto MAC address learning
F) All of the above
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Which set of actions satisfy the requirement for multifactor authentication?
A) The user enters a user name and password, and then re-enters the credentials on a second screen.
B) The user swipes a key fob, then clicks through an email link.
C) The user enter a user name and password, and then clicks a notification in an authentication app on a mobile device.
D) The user enters a PIN into an RSA token, and then enters the displayed RSA key on a login screen.
F) A) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
Refer to the exhibit. Which two statements about the interface that generated the output are true? (Choose two.) 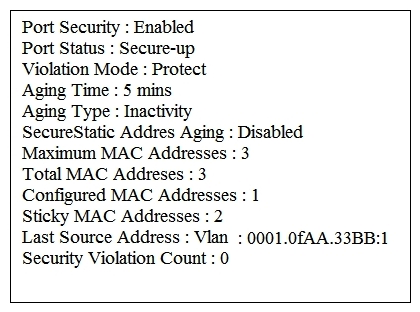
A) learned MAC addresses are deleted after five minutes of inactivity
B) the interface is error-disabled if packets arrive from a new unknown source address
C) it has dynamically learned two secure MAC addresses
D) it has dynamically learned three secure MAC addresses
E) the security violation counter increments if packets arrive from a new unknown source address
G) B) and C)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
 Refer to the exhibit. The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router. Which two static host routes must be configured on the New York router? (Choose two.)
Refer to the exhibit. The loopback1 interface of the Atlanta router must reach the loopback3 interface of the Washington router. Which two static host routes must be configured on the New York router? (Choose two.)
A) ipv6 route 2000::3/128 s0/0/0
B) ipv6 route 2000::1/128 s0/0/1
C) ipv6 route 2000::1/128 2012::1
D) ipv6 route 2000::1/128 2012::2
E) ipv6 route 2000::3/128 2023::3
G) B) and D)
Correct Answer

verified
Correct Answer
verified
Multiple Choice
 Refer to the exhibit. What is the effect of this configuration?
Refer to the exhibit. What is the effect of this configuration?
A) The switch port remains administratively down until the interface is connected to another switch.
B) Dynamic ARP Inspection is disabled because the ARP ACL is missing.
C) The switch port interface trust state becomes untrusted.
D) The switch port remains down until it is configured to trust or untrust incoming packets.
F) B) and C)
Correct Answer

verified
Correct Answer
verified
Showing 141 - 160 of 411
Related Exams